
Saferpay TLS Change
Deactivation of TLS 1.0 and 1.1
Summary
Saferpay uses the Transport Layer Security protocol (TLS) to secure the communication between merchant, customer and partner systems. According to the latest revision of the PCI Data Security Standard (PCI DSS v.3.2), 30 June 2018 is the deadline for disabling early revisions of the TLS protocol (more information here and here).
In order to ensure PCI DSS compliance and continue offering the highest security standards to our customers, Saferpay will deactivate TLS 1.0 and TLS 1.1 encryption protocols in our production environment as of June 12th 2018. All future communication with our systems will have to be encrypted using the TLS 1.2 protocol with a supported cipher suite.
Impact
What does this mean for you?
If after this date your applications and infrastructure are not capable of TLS 1.2 with a supported cipher suite, they will not be able to communicate with the Saferpay infrastructure and services and you will not be able to process ANY payments.
If there is uncertainty as to whether changes need to be made to your system, please consult your technical operator or administrator.
Is there a need for action?
Do you use a hosting provider (For example Strato/1&1, ePages etc.)?
YES
Contact your provider and ask them, if they support TLS 1.2!
NO
Does your system already support TLS 1.2 using one of the supported cipher suites?
If yes, no further action is required. If no, then update your system, so it supports TLS 1.2 accordingly. You may need to contact your system-administrator for help, so he/she can update your system to support TLS 1.2.
NOTE: Information about how to check your system can be found under Technical Details further down.
Details
As of June 12th 2018 all communication with Saferpay will have to be encrypted using the TLS 1.2 protocol with one of the supported cipher suites. The affected functionality includes all services offered by Saferpay:
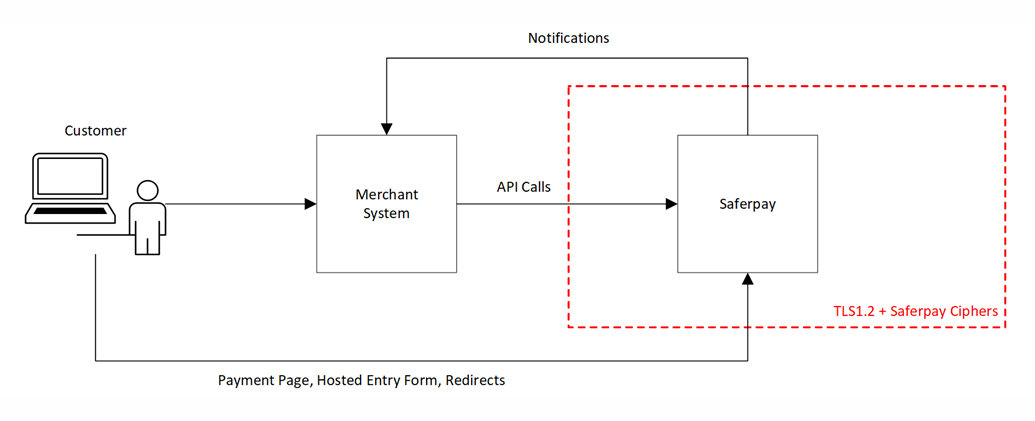
- HTTPS requests from merchant systems to Saferpay
- API requests and Lib calls (JSON API, HTTPS Interface, .NET/Java Client Library)
- Payment Page, Hosted Entry Form and various redirects to www.saferpay.com
- HTTPS requests from Saferpay to merchants systems
- Notifications (e.g. callback URLs given in the NOTIFYURL parameter)
To ensure that your systems are compliant, we recommend an integration test against our test environment, which has already been configured to only allow TLS 1.2 connections. Make sure you go through the whole payment process i.e. also testing actions performed by ERP systems for example.
Cipher suites supported by Saferpay
Following the change on 5th June 2018 Saferpay will support the following cipher-suites for establishing TLS 1.2 connections:
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P521
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P521
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P521
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
Testing procedure
Please consider the following steps, when testing your systems:
- If you haven't already, please register for your own personal test account here: https://test.saferpay.com/
- Please ensure, that your system (e.g. shop software) is set to test mode and enter the credentials of your test account, which you will receive via email, inside your administration backend of the shop.
In the case of your shop not offering a dedicated test mode, please follow the following guide (See Older API => Saferpay Client Libraries). When in doubt, you may need to contact your development department, so they can help you with that.
- Execute a full payment. If it is successful, your system is prepared for the coming change.
Using TLS 1.2 with Saferpay interfaces
Remarks on application environments
Some application environments may need general configuration steps in order to be able to handle TLS 1.2.
First make sure, that your environment is set up correctly, then proceed to the specific interface further down.
Environments using Java
If your Java Runtime Environment is at least Java 8, no customizations are necessary. Java 8 uses TLS 1.2 by default.
In environments using Java 7, the use of TLS 1.2 must be explicitly activated. The console command for this is:
- java.exe -Dhttps.protocols=TLSv1.2
Earlier versions of Java do not support TLS 1.2. The Java client can no longer be used in these environments.
Environments using .NET
For .NET framework version 4.6 and higher, no customisations are necessary. TLS 1.2 is then used by default.
In environments using the .NET framework 4.5, the use of TLS 1.2 must be explicitly activated. Please insert the following command into your application:
- ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
Earlier versions of the .NET framework do not support TLS 1.2. The .NET client can no longer be used in these environments.
Saferpay Java Client
Support for TLS 1.2 for the Java Client Library depends on the version of your Java Runtime Environment. See Environments using Java above, for more information.
Please note that the Java Client is obsolete and is no longer updated with any additional functions or improvements. We recommend a changeover to our modern and secure JSON API.
Saferpay .NET Client
Please note that the .NET Client is obsolete and is no longer updated with any additional functions or improvements. We recommend a changeover to our modern and secure JSON API.
Saferpay HTTPS Interface/Hosting Service
When using the https interface, it depends in particular on the environment you use. The documentation available for this might provide information about whether your environment can use TLS 1.2 or not.
For testing you will need a special legacy account which you can find here. Please see Testing procedure for further details.
Please note that the HTTPS Interface is obsolete and is no longer updated with any additional functions or improvements. We recommend a changeover to our modern and secure JSON API.
Batch Processing
Integrations that automatically call up the batch processing interface must use an HTTP client that supports at least TLS 1.2. You can find details in the documentation of your application framework.
The use of the batch processing interface via a web browser requires a TLS 1.2-enabled browser. All modern browsers already support TLS 1.2. You can find a list of supported browsers here.
X-Terminal and MPO Easy
MPOEasy and X-Terminal will no longer be supported. Affected customers were informed in advance.
Alternatively the secure and convenient mail/phone order functionality of the Saferpay Backoffice can be used in your web browser.
C++ Client
The C++ client was discontinued in 2010 and is no longer supported.
We strongly recommend a changeover to our modern and secure JSON API.