In an increasingly digital world, with more information about individuals being collected every day, it is natural that innovators will start to make use of these new data sources. As these changes occur, further questions arise on individual and societal privacy.
As more and more data is collected, systems become exponentially complex as more services move online and collaboration increases. It is difficult or sometimes infeasible to guarantee that operations are running as expected and that no fault will occur. For this reason, it is paramount that organisations integrate security and privacy guarantees by design and by default. Not only to comply with the regulation that requires that personal data is protected but also to maintain and verify the security of the systems they operate.
The impact of technology on privacy
For over a century technological developments have led to new privacy concerns.
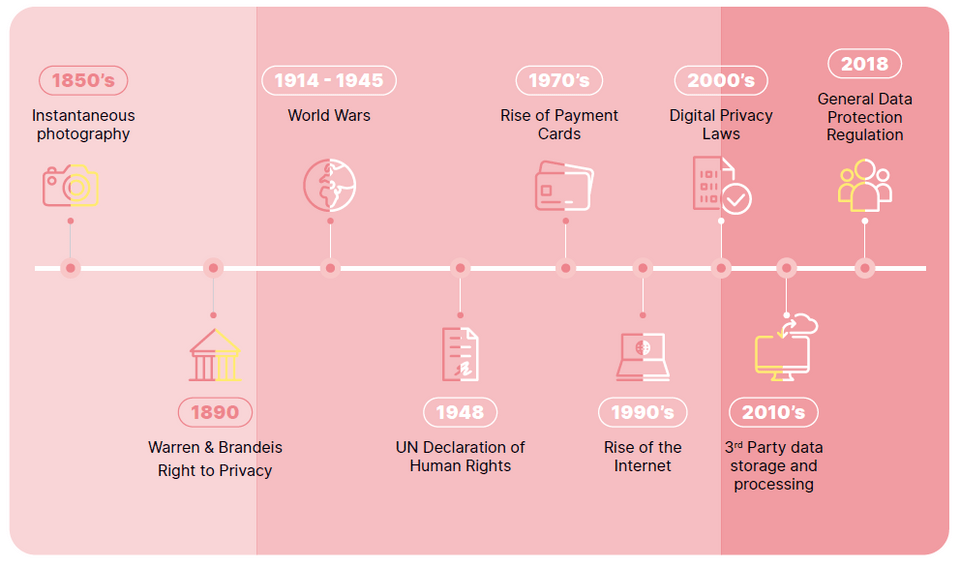
The legislative and technological evolution of privacy
The development of the Internet and the spread of personal computers in the early 1990s was the point when the line between our personal and private lives became unclear. For the first time, people at home could interact with enterprises from the comfort of their own homes. Then, with the rise of social media, people’s digital selves began to emerge.
The past decades have seen people’s lives become increasingly digitised, far beyond the realms of social media. Now, people’s health and wellbeing, education, shopping and civic activities are often carried out online, and the Covid-19 pandemic has further exacerbated this. With the maze of information and services now online, it is essential to organise it and present it to enable users to find the appropriate information for their needs.
These changes have seen a shift from the 1970s, where the main concern was how could communication be secured (including payments), to now where a key questions is how can computations be performed securely?
Trends and challenges
The fundamental advances, both in terms of regulation and technology, that we expect to gain momentum are:
- Privacy by design - There is a responsibility to build products with the principles of privacy by design. As new services are designed and built, privacy is embedded into their foundations.
- Automated regulation - To comply with regulation, increase efficiency, and protect the trust of a brand, regulatory rules should be included in the construction of new services and their computational flows.
- Advanced functionality (traceability, auditing, and accountability) - New methods balance the need for privacy and regulatory control. Should something go wrong in a process, the data can be protected while tracing the cause.
To ensure that products protect privacy, some of the most noteworthy emerging tools include:
- Differential privacy – Allows the addition of some randomly selected noise to data to compute privacy-preserving statistics. Although the resulting statistics will not be exact, they will be close to the actual value and guarantee that no individual can be identified from the result.
- Advanced encryption: homomorphic encryption - Allows computation directly on encrypted data. This means that an analyst will never see the underlying personal data.
- Advanced encryption: functional encryption - Allows computation of certain functions on encrypted data, thereby granting fine-grained access control to the person or team conducting the analysis.
- Multiparty computation - This allows computation on encrypted data stored in multiple locations. This gives greater security and privacy guarantees.
- Privacy-preserving machine learning and federated learning - Aims to protect the security, privacy, and confidentiality of data, while still allowing useful analytics or predictive models to be developed.
- Combining these tools allows complex systems to be built that enable privacy preserving computation that was infeasible a few years ago.
- Finally, zero-knowledge proofs is a technique that could be one of the most disruptive in the coming years. Although zero-knowledge proofs are not completely new in the field of cryptography, they have recently gained much attention, resulting in efficiency advances and their use in a broader scope of scenarios.
- A zero-knowledge proof is a cryptographic protocol that allows users to prove their knowledge of a certain piece of (potentially secret) information, without conveying anything other than the fact that they know the information.
- For example, when registering to access websites online, a lot of personal information (name, age, address) is needed to create an account. The argument for requiring so much information is often to prove some attribute (e.g. most social networks require users to be over 13).
- A zero-knowledge proof would allow a user to provide “proof” that they are over 13 without needing to reveal their date of birth.